Security Researcher 🔓

My name is Vladimir Smitka and I’m a security researcher/hobbyist from the Czech Republic. I specialize in WordPress security&performace and secure infrastructure for running websites. I do massive scans of the internet for my research. I’m also the owner of Lynt, a PPC Agency and Spirit Radar, a global service for tracking prices of Rums and Whiskies. I’m also an active member of the Czech WordPress community and one of the WordCamp Prague organizers. For a quick understanding of my approach, check out my WordCamp EU security talk.
Blog
Latest articles on bugs found, scan results and tips.
-

Vladimir vs Hosting Industry – PHP & system functions
Read more: Vladimir vs Hosting Industry – PHP & system functionsIn the previous part of this series, I repeatedly mentioned that users should not have access to PHP-FPM sockets, not even their own. The main reason is that direct communication with the PHP-FPM socket can influence PHP settings and bypass various restrictions. For example, it can bypass open_basedir limitations or enable system functions that are…
-

Vladimir vs Hosting Industry – PHP FPM Unix Socket
Read more: Vladimir vs Hosting Industry – PHP FPM Unix SocketIn my previous article, I demonstrated how I managed to attack a Docker container due to a publicly accessible PHP-FPM socket on a TCP port. However, in traditional (non-containerized) infrastructure, Unix sockets are more commonly used. These sockets behave similarly to regular files with various permissions. The permissions of these Unix sockets are absolutely critical,…
-

Vladimir vs Hosting Industry – Docker & PHP FPM
Read more: Vladimir vs Hosting Industry – Docker & PHP FPMIn the teaser article, I discussed my research on various CloudPanels, where I attempted to bypass the isolation of individual sites and to make unauthorized modifications. Following the teaser’s release, many users were surprised to learn that this issue also occurred with providers using Docker, who often claim their service is completely secure thanks to…
-

Teaser: Vladimir vs Hosting Industry
Read more: Teaser: Vladimir vs Hosting IndustryProper site isolation is crucial for web hosting security, but my investigation revealed alarming weaknesses in popular providers’ isolation mechanisms. By exploiting misconfigurations, I easily bypassed barriers between sites, accessed sensitive data, and even compromised entire hosting infrastructures within minutes.
-
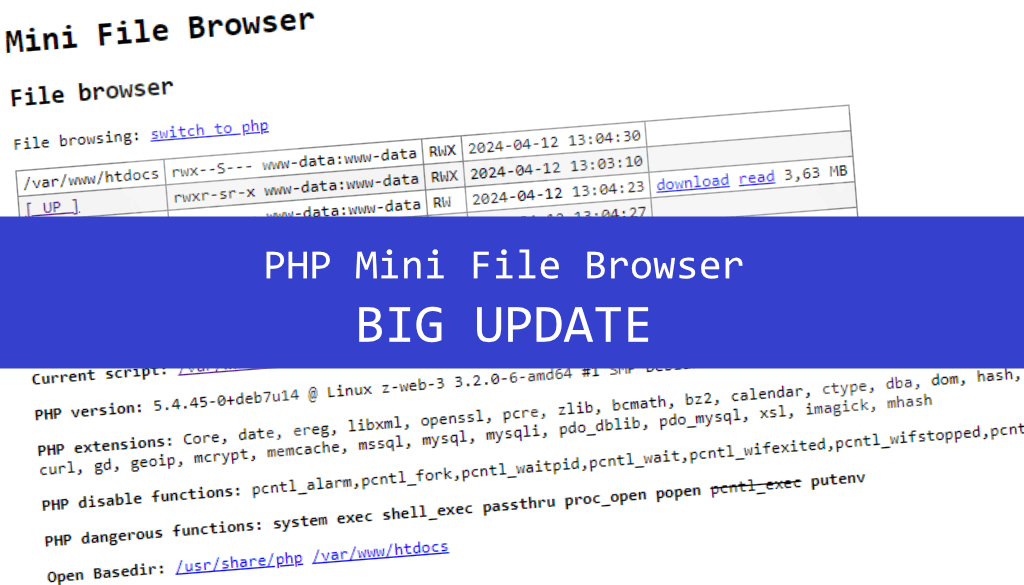
PHP Mini File Browser Update
Read more: PHP Mini File Browser UpdateWhen testing the security of PHP/WordPress sites, I am usually first interested in the environment where the site runs and the structure of the application. To simplify the initial audit, I wrote a mini PHP file browser for myself in 2014 (I put it on GitHub in 2016). Since then, there have been only few…
-

13 extra things we do for better WordPress Security
Read more: 13 extra things we do for better WordPress SecurityLooking beyond basic tips, here are 13 extra measures based on years of experience to fortify your WordPress security.
-
WordPress Builders: journey from phpinfo() to RCE
Read more: WordPress Builders: journey from phpinfo() to RCEIn the context of the recent surge in attention towards a critical Remote Code Execution (RCE) flaw in Brick Builder, I want to shed light on a less-known issue I discovered and reported two years ago. This flaw, which has been quietly addressed in versions around 1.6, affects not only Brick Builder but also other…
-

Hello, Unauthenticated RCE here! What to do?
Read more: Hello, Unauthenticated RCE here! What to do?Last week we witnessed a critical vulnerability in the WordPress visual builder Bricks: https://snicco.io/vulnerability-disclosure/bricks/unauthenticated-rce-in-bricks-1-9-6. In this article I will describe how the attack happened, add a bit of theory for those who are not so tech-savvy, add procedures for cleaning up the site and tips for preventing future attacks. What happened? Due to the severity…
-
WordPress installer attack race
Read more: WordPress installer attack race“The Famous WordPress 5-Minute Install” was great. Unfortunately, today it can cause serious security problems. The typical scenario is to upload core files to your host, open the installer, and it is done in a few minutes. During these few minutes is your installer publicly available to everyone. If the attacker is speedy enough, he…
Subscribe
Enter your email below to receive updates.